|
|
Event Review
In mid-May of 2024, the GoEdge QQ group was disbanded and the group leader SuperG lost contact on May 20th. On that day at 9 am and 6 pm, updates were released in the chat group, including the following:
On May 20th at 9 am, an update version of 1.3.9 was released for the node program file. The MD5 hash of the edge-node file is 8EBAC47C212DBB41CC0B2B9C6D4B32E4. The MD5 hash of the node program archive is D6B495249683D981DEA15B5BAD97ACDB.
The management platform update was uploaded around 6 pm, with a node program archive attached, which was intended for use by the edge-api. However, the date when the node program was modified was actually at 6 PM, not admin's proximity.
This seems to be wrong, could it have been a private goods drop-in? The report shows that there was an updated URL for the node program string, as follows:
[ol]https://cdn.jsdelivr.vip/jquery.min-3.7.0.js
[/ol]
It appears that the CDN resource used is from jsdelivr. This service is indeed very kind, but it also seems like some sort of virus may have been implanted into the server ssh password.
On July 22nd, GoEdge's Telegram group returned. After several days of silence, GoEdge users noticed that their websites had inserted a piece of JavaScript code at the end of the page.
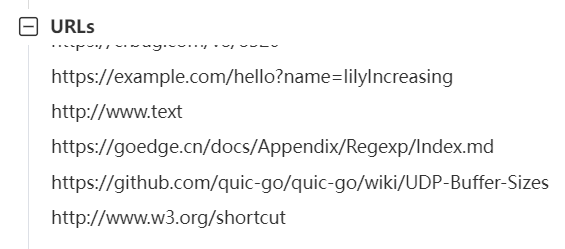
Firstly, we need to analyze the MD5 hashes of the node program files. We found that the strings of the node programs contained such a URL:
[ol]https://cdn.jsdelivr.vip/jquery.min-3.7.0.js
[/ol]
Based on the current situation, we only need to look whether there is any URL in the node program string. Whether or not the backdoor exists, we can't tell. Let's take a look at the report and see the URLs extracted by the sandbox.
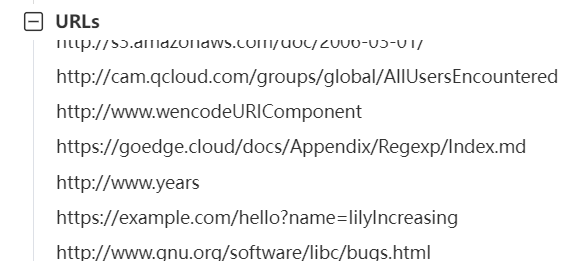
Then, we need to check if there are any different URLs between the two versions, which are the node program files from May 20th and the one from June 6th. There seems to be nothing different about them except for the domain change, going from cn to cloud. I think we should keep this question open until further analysis. Based on my memory, after a few days of silence, GoEdge's Telegram group returned again. After compiling and publishing for several days, the MD5 hash of the node program changed, and the modification date became May 24th.
Recently, many GoEdge users have discovered that their websites would insert a piece of JavaScript code at the bottom of the page. Firstly, let's analyze the MD5 hash of the node program file.
There were many GoEdge users who discovered that their websites' footer would add a piece of JavaScript code. Firstly, let's analyze the MD5 hash of the node program file.

We first analyzed the MD5 hash of the node program file on May 20th, and then analyzed the MD5 hash of the node program file on June 6th. In the former case, we found that the string of the node program contained the following URL:
[ol]https://cdn.jsdelivr.vip/jquery.min-3.7.0.js
[/ol]
According to the current situation, we only need to look whether there is any URL in the node program string. Whether or not the backdoor exists, we can't tell. Let's take a look at the report and see the URLs extracted by the sandbox.

Next, we need to check if there are any different URLs between the two versions, which are the node program files from May 20th and the one from June 6th. There seems to be nothing different about them except for the domain change, going from cn to cloud. I think we should keep this question open until further analysis. Based on my memory, after a few days of silence, GoEdge's Telegram group returned again. After compiling and publishing for several days, the MD5 hash of the node program changed, and the modification date became May 24th.

As mentioned earlier, GoEdge users frequently reported that their websites' footers would insert pieces of JavaScript code at the bottom of the page. Firstly, let's analyze the MD5 hash of the node program file.

After the 26th日凌晨,有用户发现自己的网站结尾处插入了私货。经过大家的讨论,发现了这样的代码:
```javascript
window.location.href = 'http://example.com';
```
From the境内访问,这个网址是一个混淆加密的js文件。从境外访问,不允许访问,这......群主不是说要只给海外用户提供服务嘛。群主在北京时间12:50上传了一个无毒的版本,试图掩盖一切。然后,随着一声“不信谣,不传谣”,群人数大大减少,大概是大家自己退群了吧。
How do we solve this?
Based on our previous analysis, only the node program file contained malicious content, so we suggest all nodes revert to the version on May 20th, avoiding the backdoor. If you installed after May 21st, please immediately revert. Here, thank you for sharing the Google Drive archive of the GoEdge team
To ensure that curl and unzip are already installed, let's first make sure that GoEdge's DNS name is blocked. Execute the following command:
echo "127.0.0.1 goedge.cloud" | sudo tee -a /etc/hosts > /dev/null
echo "127.0.0.1 goedge.cn" | sudo tee -a /etc/hosts > /dev/null
Next, let's return the main control to the version on May 20th
To execute the following steps, please refer to the instructions provided by the owner of the GoEdge team. If you don't trust me, please replace your own URL with the one provided by the owner of the GoEdge team.
Here, we'll demonstrate how to install the AMD64 architecture version of the node program using the CDN resource provided by the owner of the GoEdge team. For other architectures, please follow the same process as above.
Before proceeding, please note that we deleted the GoEdge's usr directory because according to my experience, the automatic upgrade of nodes may cause duplicate installations. Specifically, what exactly happened during the installation of the node program is still unclear; we also deleted the /opt/cache directory, which is the default caching directory. If you have other caching directories, please clear them out. If they're too large, please just reinstall the system. |
|